Deception360™
Deception Cybersecurity
PacketViper Deception360™ is an active and agentless deception cybersecurity solution combining internal deception with the industry’s only active exterior facing deceptive capabilities. The cyber deception solution acts early in the cyber kill chain during the reconnaissance phase of a cyber-attack. Using deceptive elements to emulate a Moving Target Defense (MTD), Deception360 enables operators to detect, prevent, respond, and contain threats automatically based on truly native capabilities and without complex orchestrations with other security tools and technologies. The effectiveness of this deception in every direction approach is derived from a lower level of interaction with threats using deceptive elements that are lightweight, software-based, and easily deployed on both sides of any network boundary.This ability to use deception not only inside but outside the network gives PacketViper users not only detection of east-west activity inside their networks but north-south activity into and out of their internal networks from the Internet. We call this Deception360.
Shortest Time to Greatest Value
PacketViper Deception360 allows clients to derive immediate value from their deception solution deception due to the unique combination of prevention, detection, and the ability to respond without complex orchestrations. The graph represents the comparison between PacketViper Deception360 and more traditional internally oriented, detection-only deception solutions.
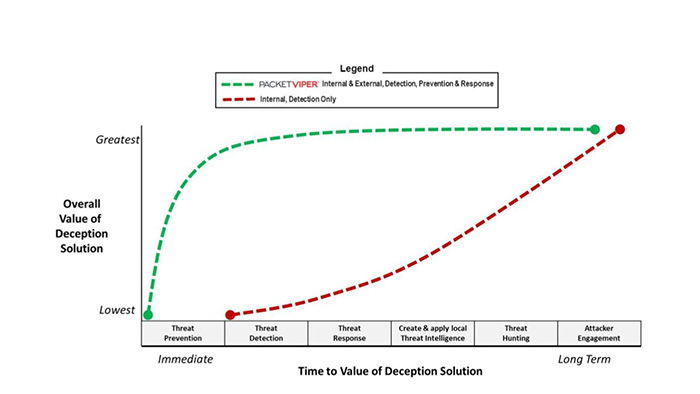
Traditional deception solutions from deception technology vendors tend to be costly, complex, agent-based, and require highly sophisticated teams to be effective. Even with all of that support infrastructure in place, the time it takes for those organizations to realize demonstrable value is prolonged. It is even possible to deploy those types of deception solutions and never see actual results, especially if the deployment is limited in scope due to budget and time resources. Conversely, PacketViper Deception360 is extremely cost effective, lightweight in nature, saturation friendly, and delivers immediate, measurable security results, which support PacketViper’s mission of providing better, faster security.

Traditional deception solutions from deception technology vendors tend to be costly, complex, agent-based, and require highly sophisticated teams to be effective. Even with all of that support infrastructure in place, the time it takes for those organizations to realize demonstrable value is prolonged. It is even possible to deploy those types of deception solutions and never see actual results, especially if the deployment is limited in scope due to budget and time resources. Conversely, PacketViper Deception360 is extremely cost effective, lightweight in nature, saturation friendly, and delivers immediate, measurable security results, which support PacketViper’s mission of providing better, faster security.
Deception Outside the Box:
Internal and External Defense
A Deception Solution that can be Deployed Early and Often
Internal decoys detect and respond to threats moving laterally within the network with virtually no false positive results. Threats are automatically stopped from exfiltrating data or establishing command and control communications.
External decoys create the appearance of a moving target at the network edge by automating when and how decoys respond to whom, and when to act. These dynamic perimeters make the network harder to size up and keep threats off the network.
This approach complements the traditional security stack while eliminating the attacker’s ability to operate anonymously and severely limiting global attack vectors.
The diagram below depicts the benefits of Deception360 when functioning inline both internally and externally:
Heavyweight Results
The use of PacketViper Deception360 to enable threat detection, prevention, response, and containment in addition to delivering high fidelity internal threat detection, are benefits we refer to as ‘heavyweight results. The preventive actions and responses executed straight from Deception360, without complex orchestrations with other security tools, and can range from routing threats into specific areas of the network, or limiting their access to the network, and extend all the way to outright blocking them.
By identifying and acting against threatening activity very early in the cyber kill-chain and preventing further progress, a would-be attacker's ability to gain an understanding of the underlying assets in a network, identify vulnerabilities, probe for misconfigurations, and run remote exploit attempts is eliminated. Based on the broad application of Deception360, and our placement within the security stack PacketViper can detect, respond, and block threats at wire speed.
No Security Orchestration, Automation, and Response (SOAR) infrastructure, tools, or processes are required to respond to threats with Deception360. Action is taken based on client policies at wire speed.
Indicators of Compromise (IOCs), as well as locally harvested, machine-readable threat intelligence (MRTI) is immediately applied, and can be provided to other security controls within your security program.
The proactive use of the insights gained from deploying Deception360’s lightweight deception artifacts acts as a force multiplier to existing security controls by not only providing dynamic defense capabilities, but by also improving operational efficiencies and producing measurable hard-dollar cost-savings.
A genuine return on investment (ROI) can be attained through the elimination of what is at best unnecessary, and at worst malicious activity from the environment. This greatly reduces noise on the firewall, clutter in the SIEM, and mountains of off-target and false-positive events and alerts that security teams must store and analyze in order to detect threats.
By identifying and acting against threatening activity very early in the cyber kill-chain and preventing further progress, a would-be attacker's ability to gain an understanding of the underlying assets in a network, identify vulnerabilities, probe for misconfigurations, and run remote exploit attempts is eliminated. Based on the broad application of Deception360, and our placement within the security stack PacketViper can detect, respond, and block threats at wire speed.
No Security Orchestration, Automation, and Response (SOAR) infrastructure, tools, or processes are required to respond to threats with Deception360. Action is taken based on client policies at wire speed.
Indicators of Compromise (IOCs), as well as locally harvested, machine-readable threat intelligence (MRTI) is immediately applied, and can be provided to other security controls within your security program.
The proactive use of the insights gained from deploying Deception360’s lightweight deception artifacts acts as a force multiplier to existing security controls by not only providing dynamic defense capabilities, but by also improving operational efficiencies and producing measurable hard-dollar cost-savings.
A genuine return on investment (ROI) can be attained through the elimination of what is at best unnecessary, and at worst malicious activity from the environment. This greatly reduces noise on the firewall, clutter in the SIEM, and mountains of off-target and false-positive events and alerts that security teams must store and analyze in order to detect threats.
Deceiving and Misleading Threats Throughout the Attack Cycle
Cost-savings will be realized through the entire security program’s processes, less unwanted traffic processed and logged by the firewall, fewer logs accumulating in a SIEM tool and storage, fewer SIEM events to be triaged and dispositioned by SOC analysts.
Deception Enabled Detection, Prevention, Response and Containment
PacketViper’s deception technology solution, Deception360™ , is very different in method and implementation from deception solutions that only provide internal threat detection. Deception360 truly provides automated, deception enabled threat detection, prevention, and response both internally and externally. Other deception technologies only support an internal threat detection use case.
A brief summary comparison of PacketViper deception enabled threat detection, prevention, and response and an ‘internal threat detection only’ common deception solution is as follows:
Internal threat detection-only focused deception technologies are characterized by the following:
PacketViper’s Deception360 deception-enabled threat detection, prevention, response, and containment capabilities focus on the following:
A brief summary comparison of PacketViper deception enabled threat detection, prevention, and response and an ‘internal threat detection only’ common deception solution is as follows:
Internal threat detection-only focused deception technologies are characterized by the following:
- Strictly focused on internal threat detection. Other deception tolls don’t go to work until the threat is on the network.
- Providing a very narrow field of view based solely on the decoys and artifacts themselves.
- Creating, re-creating, and constantly chasing highly detailed decoys that will withstand continued scrutiny and engage attackers on the network.
- Providing alert-only feedback, relying on expensive threat hunters and analysts to do something with TTP, IOCs, and other artifacts.
- Responses to identified threats require integration, orchestration and/or manual intervention processes.
PacketViper’s Deception360 deception-enabled threat detection, prevention, response, and containment capabilities focus on the following:
- The ability to deploy decoys, sensors, deceptive artifacts, and continuously moving deception techniques on a network boundary to obfuscate the network and prevent external threats from entering.
- Internal threat detection, prevention, response, and containment without orchestration with any other security tools or processes.
- Increased transparency into all network traffic, not just that which interact with deceptive elements.
- Easily supporting saturation-levels of deployed Sensors, Decoys, Sirens and Deception360 artifacts that identify unwanted and potentially malicious traffic on the network.
- Stopping attackers very early in the cyber kill-chain before they get a chance to mount an effective attack.
- Added context to network traffic to enable shaping based on not just decoys but through source geography and organization-based policies
Deception360 is able to deliver so much more value because it deploys in-line between two or more networks. This inline position, deployed most commonly as in invisible and undetectable bridged connection between network boundaries means that attacks can be blocked, at network speed. In addition to outright blocking, attackers can alternatively be routed to sandbox segments for further analysis or slowed (a function we call tarpitting) depending on security objectives.
A Flexible Tool for Insight
Finally, PacketViper Deception360 is built as a flexible tool that enables security professionals to gain immediate insight into the networks they are protecting, the assets on those networks, and the traffic flows that happen between them and the outside world. This insight is delivered via a series of highly customizable and interactive dashboards, BI-like analytics and interrogation tools, and several layers of reporting capabilities.
Decoys, Sensors, Sirens, and other deception artifacts, although a very important part of the Deception360 solution, work in conjunction with the network visibility, transparency, and context that the tool provides. With the addition of network context through the inclusion of the source and destination geographies, protocol information, direction, velocity, duration and time, entity tracking, custom context groups, operators quickly build a holistic, comprehensive view of security within their networks.
With proprietary tools like Net Check and Web analyzers, the user can be confident in what they see, and determine the appropriate policy to allow, block, monitor or control the activity.
Once the deceptive elements and behavioral policies have been deployed, Deception360 starts performing work on the operator’s behalf, continuously creating, and applying behavior-triggered new rules to stop unwanted and potentially malicious traffic in real-time at wire speed.
With easy-to-use rule expiration and rule re-creation capabilities, users can be assured that Deception360 always has up-to-date, organic threat intelligence and protection for your network, your assets, and your adversaries.
Decoys, Sensors, Sirens, and other deception artifacts, although a very important part of the Deception360 solution, work in conjunction with the network visibility, transparency, and context that the tool provides. With the addition of network context through the inclusion of the source and destination geographies, protocol information, direction, velocity, duration and time, entity tracking, custom context groups, operators quickly build a holistic, comprehensive view of security within their networks.
With proprietary tools like Net Check and Web analyzers, the user can be confident in what they see, and determine the appropriate policy to allow, block, monitor or control the activity.
Once the deceptive elements and behavioral policies have been deployed, Deception360 starts performing work on the operator’s behalf, continuously creating, and applying behavior-triggered new rules to stop unwanted and potentially malicious traffic in real-time at wire speed.
With easy-to-use rule expiration and rule re-creation capabilities, users can be assured that Deception360 always has up-to-date, organic threat intelligence and protection for your network, your assets, and your adversaries.
PacketViper and Artificial Intelligence
AI Type 1: Reactive Machine
PacketViper Deception360 utilizes Artificial Intelligence with type I wire-speed capabilities to act as a reactive machine in using the policies established by the user to react to potential threats and carry out the adaptive responses dictated by the user.
Consistent with this type of AI, PacketViper detects cyber threats directly as they interact with decoys, sensors, sirens and context filters, and acts based on that detection. This approach to AI ensures a level of reliability and consistency in that the machine (in this case PacketViper Deception360) will behave exactly the same way every time it encounters the same situation.
AI is used within PacketViper to achieve practical business results and to prevent threats. Using dynamic Moving Target Defense perimeters, PacketViper can be configured to deceive, detect, and automatically block detected activity. This dynamic approach also provides a self-cleaning process that removes stale rules while applying new rules as dictated by real-time sensor activity. This sensor capability will alter its perspective automatically to capture intelligence using different listeners based on any number of IP attributes, times, rates, volumes, directions, origins, destinations and identities to provide real-time, most accurate, and applied intelligence. Once configured, the system is fully automated and improves security posture continuously. This automation creates cycles for security practitioners to focus efforts on designing deception campaigns that actively hunt and mitigate threats.
PacketViper Deception360 utilizes Artificial Intelligence with type I wire-speed capabilities to act as a reactive machine in using the policies established by the user to react to potential threats and carry out the adaptive responses dictated by the user.
Consistent with this type of AI, PacketViper detects cyber threats directly as they interact with decoys, sensors, sirens and context filters, and acts based on that detection. This approach to AI ensures a level of reliability and consistency in that the machine (in this case PacketViper Deception360) will behave exactly the same way every time it encounters the same situation.
AI is used within PacketViper to achieve practical business results and to prevent threats. Using dynamic Moving Target Defense perimeters, PacketViper can be configured to deceive, detect, and automatically block detected activity. This dynamic approach also provides a self-cleaning process that removes stale rules while applying new rules as dictated by real-time sensor activity. This sensor capability will alter its perspective automatically to capture intelligence using different listeners based on any number of IP attributes, times, rates, volumes, directions, origins, destinations and identities to provide real-time, most accurate, and applied intelligence. Once configured, the system is fully automated and improves security posture continuously. This automation creates cycles for security practitioners to focus efforts on designing deception campaigns that actively hunt and mitigate threats.