FOR SALE: A much smaller cybersecurity haystack
January 9, 2023
Far too many cybersecurity leaders are going to ask their executive teams for drastically increased security budgets THAT DON’T REDUCE THE SECURITY BURDEN. Increases in cybersecurity budgets frequently only buy faster hamster wheels.
Think about the typical activity at the perimeter, or frontline, of your network. This is where the cyber burden-cycle truly starts (IT analysts espousing a borderless world notwithstanding).
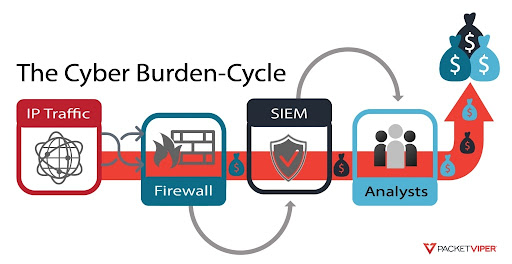
- IP traffic your enterprise doesn’t want or need hits your firewall in the form of a scan or a probe.
- Firewall drops it, meaning the specific connection request is dropped but the offender IP is still out there reloading to make another connection request that your firewall might allow – this process repeats endlessly at wire speeds.
- Each drop event consumes firewall resources.
- Each drop event is a logged event that lands in your SIEM.
- Each event is indexed, analyzed and stored BEFORE an overworked analyst can review it.
The insult on top of the injury is that most of these events are irrelevant to your business. All of these events are inflating your costs, depleting your resources and clouding your ability to see real threats.
So, what are the options?
Option 1: Beef up the firewall.Result: Bigger firewalls will drop more connections faster. Costs escalate. The burden still exists.
Option 2: Expand the SIEM.
Result: Expanded SIEM means a larger haystack and less visible needles. Costs escalate. The burden still exists.
Option 3: Hire more analysts.
Result: You can never hire enough, even if you could find and afford them. Costs escalate. The burden still exists.
Option 4: Better, more curated threat intelligence.
Result: Intelligence gets stale quickly and may not be relevant to your enterprise in the first place. Costs escalate. The burden still exists.
The best possible outcome in this scenario is treading water. The more likely reality is that while costs are increasing, you continue to fall behind more every day.
It is time to stop the madness.
Start with shedding the volumes of unwanted, uninvited traffic – before the firewall. PacketViper provides the context that enables you to translate business requirements into technical controls. Context around companies you want to work with that might have locations in countries you otherwise have no need for. Context that enables an attacker to be dynamically identified and disrupted in the reconnaissance phase of the cyber kill chain. And context that enables an escalating response commensurate with the degree of risk you’re willing to assume.PacketViper provides context that reduces the burden your organization, your infrastructure, and your teams are subjected to every minute of every day.
You can continue to go faster and bigger to sift through a larger and larger haystack, but at PacketViper we believe a smaller haystack acts as a force-multiplier for all the investments you have already made in security and compliance.
Wouldn’t that be a refreshing message for the board and other executives to hear?
Previous Post
January 2, 2023
Next Post
January 16, 2023
