Deception Gets Screen Time at Gartner Security Risk and Management Summit 2019
January 16, 2023
As I recap the Gartner® Security and Risk Management Summit 2019 event, one of the game changers for the market place was to see deception prominently referenced in the keynote presentation and a few other sessions. As one of three key ways organizations can utilize automation, deception was said to increase the ability to detect attacks in an efficient and cost-effective manner. Gartner Sr. Director Analyst Gorka Sadowkski discussed how deception tools could detect attacks with low/no false positives and 100% accuracy.
The example in the opening keynote described a more traditional use case for deception that keyed in on internal threat detection and then required integration and orchestration to take action on the locally generated threat intelligence. You tend to see this use case executed in very large organizations with sophisticated security operations. For the masses seeking to use deception and shorten the time to value, we offer our PacketViper Deception360 solution, where you get deception-based Detection, Prevention AND Response built into one package. No complex integrations or orchestrations required. Detect and prevent threats while automatically responding by applying locally sourced threat intelligence at wire speed, through a series of adaptive responses, either inside your network or on the perimeter.
If you like the idea of using time-proven deception techniques handed down from the likes of Sun Tzu and other battle strategists, but need your cybersecurity investments to have a more immediate payoff, check out the graphic below. The PacketViper combination of deception-based detection, prevention and response is the deception solution that produces the shortest time to the greatest value.
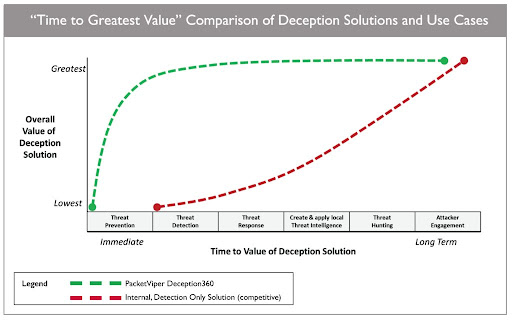 The challenge with internal, detection-only deception solutions (the red dotted line) is that it takes extended time to drive the higher fidelity alerts. Time to value is prolonged as responses to threats require resources for integration, orchestration and change control management. These solutions tend to drive the most value in very large, sophisticated organizations where the value comes from resource intensive threat hunting and attacker engagement.
The challenge with internal, detection-only deception solutions (the red dotted line) is that it takes extended time to drive the higher fidelity alerts. Time to value is prolonged as responses to threats require resources for integration, orchestration and change control management. These solutions tend to drive the most value in very large, sophisticated organizations where the value comes from resource intensive threat hunting and attacker engagement.
In contrast, PacketViper Deception360 combines internal and external detection, prevention and response (the green dotted line) to drive to the greater value in the shortest amount of time. Using deception for detection and prevention with automated adaptive responses totally inverts the ‘time to greatest value’ curve.
This approach quickly strengthens the overall security posture and board members appreciate the shorter time to value and quicker ROI.
At the event, Gartner continued to push the strategic approach they are championing called CARTA. It has seven imperatives that I will boil down into the following:
There were several different talks that either directly touched on DevOps, Security in DevOps, or DevSecOps and how it is changing how security is getting built into application development and system updating/patching.
At PacketViper we embrace the DevOps and particularly the DevSecOps mantra as a way of shortening our development cycles for PacketViper Deception360 while ensuring that we are shipping secure code and systems to our customers.
As we expand the reach of PacketViper beyond on-premise, VMWare and AWS cloud implementations into Azure cloud and explore potential integrations into Kubernetes and other containerization solutions, the ability to automate the development, deployment, and management pipelines requires a high degree of integration and automation.
We look forward to continuing to hone these pipelines and dedicate our time to making the PacketViper Deception360 solution a fuller and richer deception technology while continuing to take action to stop threats in their tracks. See for yourself by requesting a demonstration.
The example in the opening keynote described a more traditional use case for deception that keyed in on internal threat detection and then required integration and orchestration to take action on the locally generated threat intelligence. You tend to see this use case executed in very large organizations with sophisticated security operations. For the masses seeking to use deception and shorten the time to value, we offer our PacketViper Deception360 solution, where you get deception-based Detection, Prevention AND Response built into one package. No complex integrations or orchestrations required. Detect and prevent threats while automatically responding by applying locally sourced threat intelligence at wire speed, through a series of adaptive responses, either inside your network or on the perimeter.
If you like the idea of using time-proven deception techniques handed down from the likes of Sun Tzu and other battle strategists, but need your cybersecurity investments to have a more immediate payoff, check out the graphic below. The PacketViper combination of deception-based detection, prevention and response is the deception solution that produces the shortest time to the greatest value.

In contrast, PacketViper Deception360 combines internal and external detection, prevention and response (the green dotted line) to drive to the greater value in the shortest amount of time. Using deception for detection and prevention with automated adaptive responses totally inverts the ‘time to greatest value’ curve.
This approach quickly strengthens the overall security posture and board members appreciate the shorter time to value and quicker ROI.
Boiling down the seven imperatives of the Continuous Adaptive Risk and Trust Assessment (CARTA)
At the event, Gartner continued to push the strategic approach they are championing called CARTA. It has seven imperatives that I will boil down into the following:
- Your security program, assessment, controls, responses all must be continuous. Point-in-time is not appropriate for our increasingly cloud-centric, service-centric world
- Build infrastructure and systems with the idea of continuously measuring risk and threats and applying controls and adaptations
- Automate as much as possible, use analytics and orchestrations to be a force multiplier and increase speed of response
- Security programs and controls must be adaptable in real time, and the responses applied must account for having less control and being proportionate to the risk
- Make security programs and controls transparent and the information available to decision makers.
- Does this engender a continuous process?
- Does this enable me to quantify how it is working?
- How flexibly can I adjust it as circumstances may change?
- How much work will it do for my team, how much will my team need to work to make it effective?
Security in DevOps or DevSecOps
There were several different talks that either directly touched on DevOps, Security in DevOps, or DevSecOps and how it is changing how security is getting built into application development and system updating/patching.At PacketViper we embrace the DevOps and particularly the DevSecOps mantra as a way of shortening our development cycles for PacketViper Deception360 while ensuring that we are shipping secure code and systems to our customers.
As we expand the reach of PacketViper beyond on-premise, VMWare and AWS cloud implementations into Azure cloud and explore potential integrations into Kubernetes and other containerization solutions, the ability to automate the development, deployment, and management pipelines requires a high degree of integration and automation.
We look forward to continuing to hone these pipelines and dedicate our time to making the PacketViper Deception360 solution a fuller and richer deception technology while continuing to take action to stop threats in their tracks. See for yourself by requesting a demonstration.
*GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
