The Ransomware Threat to Operational Technology (OT) Networks
Ransomware is one of the most potentially damaging threats facing businesses and critical infrastructure organizations today. It is a scheme intended to harm, leveraging malware that infiltrates a target network and prevents access to vital systems. The threat then extorts money from the target in exchange for return of network asset control or destruction of exfiltrated data.
While ransomware has been a prominent IT threat for some time, cybercriminals are now increasingly targeting OT with ransomware. In one widely publicized case, packaging giant WestRock (NYSE: WRK)[1] was hit with ransomware, critical processes were hampered, and the stock dropped more than 4% the day after the breach was disclosed. There are weekly reports of organizations across every critical infrastructure vertical facing the same set of circumstances.
OT is a ripe target is because most of the focus in control environments has been on process efficiency and production uptime, not necessarily on securing the networks and critical assets that comprise the environment. OT-related equipment tends toward useful economic service life spans that far outlive their IT counterparts. Since updating OT assets with new versions and patches for vulnerabilities can result in unplanned downtime, OT environments are not patched or updated as frequently as occurs in IT. Finally, OT and IT convergence increases the potential attack surface by creating new pathways and access points for threats to infiltrate networks and systems.
While ransomware has been a prominent IT threat for some time, cybercriminals are now increasingly targeting OT with ransomware. In one widely publicized case, packaging giant WestRock (NYSE: WRK)[1] was hit with ransomware, critical processes were hampered, and the stock dropped more than 4% the day after the breach was disclosed. There are weekly reports of organizations across every critical infrastructure vertical facing the same set of circumstances.
OT is a ripe target is because most of the focus in control environments has been on process efficiency and production uptime, not necessarily on securing the networks and critical assets that comprise the environment. OT-related equipment tends toward useful economic service life spans that far outlive their IT counterparts. Since updating OT assets with new versions and patches for vulnerabilities can result in unplanned downtime, OT environments are not patched or updated as frequently as occurs in IT. Finally, OT and IT convergence increases the potential attack surface by creating new pathways and access points for threats to infiltrate networks and systems.
Fundamentals of Ransomware Attacks
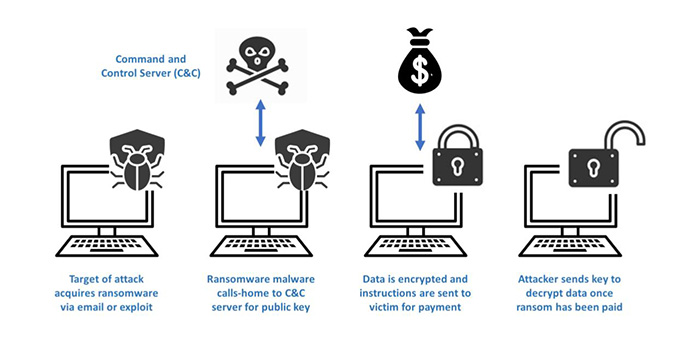
Whether the attack is on an IT or OT network, the fundamentals of ransomware attack profiles are very similar. The first stage of a ransomware attack is to infiltrate a network or facility to deploy malware. There are a variety of ways to accomplish this deposition, with the most typical approaches as part of a Business Email Compromise (BEC) or via a trusted 3rd party / vendor interaction.Once the malware has established a beach head in the target environment, it will often attempt to communicate outside of the network in order to connect to the criminal's Command and Control (C&C) server. This connection is known as the ransomware ‘call home’ and typically uses standard port 80 and HTTP or port 443 and HTTPS protocols.
The attacker then uses the C&C server to evaluate where the malware has landed within the target. The threat is now assessing the best course of action to escalate access and move laterally inside the environment to identify additional assets of value. Once the attacker has performed reconnaissance for a sufficient period of time to identify and compromise the high value assets that are likely to maximize economic gain, the threat launches the attack. The attack generally includes encryption and perhaps exfiltration of data, and potentially the functional impairment of critical equipment and assets within target environment.
Image 1 below illustrates a typical ransomware exploit:
A Practical Defense-In-Depth
Approach to Ransomware
Preventing ransomware requires a comprehensive and multifaceted security capability. A layered, defense-in-depth approach will yield the best chance to defend against ransomware in connected IT/OT networks. Endpoint-based ransomware prevention tools are important, but unpatched OT assets may not be well suited for advanced endpoint solutions. It is critical to protect the network against threats that manage to infiltrate and then seek to establish C&C communications.
PacketViper Deception Technology
PacketViper deception technology provides an active defense and counter-attack capability that is designed to identify suspicious behavior at wire speed and contain the threat so that practitioners can quickly remediate the incident. We use deception to fool the attackers by making the network difficult to see and hard to understand. Our patented technology allows users to proactively defend OT/ICS assets, remote OT endpoints, and IT infrastructures while eliminating the false-positive burden. PacketViper’s deception-enabled agentless detection, prevention, containment, and response technologies – Deception360™ and OT360™ – automate threat hunting, attack detection, and attack prevention from both external and internal threats. Our solutions provide line operators with the deception-enforced contextual security data required to act while potential threats are still in motion, and before critical OT/ICS and IT assets are completely compromised.PacketViper’s deception technology uniquely automates deception-based threat detection and attack prevention, and can be a valuable addition to a layered approach to ransomware. Agentless, software-based deception artifacts are projected into network segments and provide highly-believable and active cyber threat detection, prevention, and response. This agentless deployment mechanism allows for multi-segment network saturation without additional network noise or congestion. Both of the products provide support to help secure IT/OT alignment and can evolve from monitor-mode to active in-line security that doesn’t threaten OT uptime.
PacketViper deception uses a combination of customizable sensors, highly believable decoys with advanced capabilities, communicative Sirens™, and an array of lightweight target artifacts. Sirens are deployed in pairs that connect with one another to mimic actual data communication streams and are intended to be targets for threats passively listening to a network seeking services to exploit. Sirens are configured to emit network traffic as if it was a fully functioning system.
For threats performing more active reconnaissance scanning efforts, decoys are attractive targets. Decoys can authentically resemble systems and services that threats will try to exploit. Once decoys and sirens are probed by threats, a high-fidelity, false-positive free alert is generated, and a variety of countermeasures can be taken.
Defending Against Ransomware
Once deployed, PacketViper deceptive decoys and sensors passively monitor the network without the need for continuous scanning. This capability improves visibility while gathering intelligence on internal network threats performing reconnaissance and moving laterally through various segments. The solution can reduce threat dwell time when deployed in-line by responding to attacks at wire speeds, both within a segment or across an enterprise.Boundary protection is an important feature of PacketViper deception that utilizes a contextual network filtering engine along with deception artifacts to help contain ransomware regardless of source. A comprehensive set of rules can be easily deployed to detect anomalous outbound traffic and automatically block the C&C ‘call home’ mechanism. This approach stops ransomware from accessing the internet for host data exfiltration or leakage of proprietary information. It also prevents attack orchestration with external hosts, which blinds the attack command and control function from progress and status of the internal attack. These features serve to buy time for the impacted organization, as most ransomware attacks do not activate until a critical mass of assets are known to be compromised.
PacketViper deception technology works earlier in the cyber kill chain before threats gain access to the interior portions of the network. This deployment model allows for more effective threat detection and response, ultimately resulting in reduced risk for the organization. These capabilities can be enabled directly from all of our deception-enabled product families, and without complex orchestration or integration with any other cybersecurity or network tool.
With PacketViper’s deception technology enabled solutions, Security teams can easily and affordably saturate the network with software-based, agentless deception artifacts. Ideally, any deception strategy should include deceptive capabilities and artifacts that can spread across and saturate all network segments, including the IT/OT boundary, and any external/internal boundaries that are part of the critical environment (Image 2).
And with compliance increasingly becoming a part of comprehensive cybersecurity programs, teams find comfort in how PacketViper Deception Technology supports key existing and emerging security controls (Image 3).
This deception-based approach to ransomware defense provides new and innovative ways to address the threat earlier in the cyber kill chain, while minimizing risk and mitigating loss.