The Challenge
As operational technology (OT) assets are increasingly exposed to the internet, the reliable performance of OT networks remains essential for critical infrastructure installations, spanning a broad range of industries such as energy, utilities, transportation, and manufacturing, to name just a few.
The clear and present danger from cyber threats to our OT infrastructure resulted in the recent joint alert1 from the US National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA). The alert recommends actions against what they describe as a “perfect storm” headed towards OT owners and operators characterized by the dangerous combination of a vast and growing attach surface facing industrial operations and the fact that exploiting OT systems is easier than ever before.
Addressing these, and other specific OT security issues will require a solution that meets several key criteria which include but are not limited to the following:
A multiple context filtering, deception-enabled approach to OT security can help owner/operators address these OT security issues without threatening overall equipment effectiveness (OEE).
The clear and present danger from cyber threats to our OT infrastructure resulted in the recent joint alert1 from the US National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA). The alert recommends actions against what they describe as a “perfect storm” headed towards OT owners and operators characterized by the dangerous combination of a vast and growing attach surface facing industrial operations and the fact that exploiting OT systems is easier than ever before.
Addressing these, and other specific OT security issues will require a solution that meets several key criteria which include but are not limited to the following:
- The solution should support asset discovery.
- The solution should be vendor agnostic.
- The solution should be able to evolve from mirror mode to in-line, active security as teams come to trust it.
- The solution should work across both OT and IT environments
- The solution should be available ‘as-a-service’ for teams that are understaffed and overworked.
A multiple context filtering, deception-enabled approach to OT security can help owner/operators address these OT security issues without threatening overall equipment effectiveness (OEE).
INTRODUCING OT360™ and OTRemote™
PacketViper’s OT360 and OTRemote products represent an adaptive network security solution that monitors the OT network without active scanning. This improves visibility while gathering intelligence on network threats performing reconnaissance and moving laterally, while preserving an option to respond to attacks at wire speed - both within a segment or across an enterprise.
OT360 is designed for core facilities that are complex, multi-functional, and manned 24x7 with operators. Examples include refineries, power generation control facilities, large water and wastewater primary plant facilities, critical transportation hubs and depots, continuous production factory facilities, etc. OTRemote works in conjunction with OT360, and is designed to support smaller, usually un-attended remote facilities that are a part of a cohesive overall plant or process control environment. Examples include oil and gas well pads, water supply lift and pump stations, transportation and traffic monitoring field control devices, power distribution substations and transformer vaults, etc.
OT360 and OTRemote are lightweight, agentless, and active deception-enabled multi-context filtering solutions that act earlier in the cyber kill by chain using highly believable decoys and OT Sirens™. Sirens are intended to be targets for advanced persistent threats that are passively listening to a network, seeking systems and services to potentially exploit or attack. Sirens are configured to emit network traffic as if they were part of a fully functioning control system. Upon recognition of the siren communication stream from the siren, threats will focus efforts, enabling countermeasures to be taken. For threats performing more active reconnaissance scanning efforts, decoys present attractive targets. Decoys can resemble systems and services threats will hope to potentially exploit or attack. When threats scan a network, decoys will be discovered because they are designed to respond to various service requests as if they were a fully functioning asset. The attacker will then focus efforts on the decoy, enabling countermeasures to be taken.
Adversaries utilize deception as part of their attack methodology. It makes perfect sense for OT professionals to also leverage easy to use and deploy deceptive elements to increase attack difficulty, discover attacker patterns, and prevent future attacks. False positives are always a concern with any security tool. However, with OT360 and OTRemote, false positive events and nuisance alerts are eliminated so that operators and security teams can act with confidence on genuine on-target alerts, and have the option to easily configure the solution in-line to active blocking of attacks with automated defensive actions.
OT360 is designed for core facilities that are complex, multi-functional, and manned 24x7 with operators. Examples include refineries, power generation control facilities, large water and wastewater primary plant facilities, critical transportation hubs and depots, continuous production factory facilities, etc. OTRemote works in conjunction with OT360, and is designed to support smaller, usually un-attended remote facilities that are a part of a cohesive overall plant or process control environment. Examples include oil and gas well pads, water supply lift and pump stations, transportation and traffic monitoring field control devices, power distribution substations and transformer vaults, etc.
OT360 and OTRemote are lightweight, agentless, and active deception-enabled multi-context filtering solutions that act earlier in the cyber kill by chain using highly believable decoys and OT Sirens™. Sirens are intended to be targets for advanced persistent threats that are passively listening to a network, seeking systems and services to potentially exploit or attack. Sirens are configured to emit network traffic as if they were part of a fully functioning control system. Upon recognition of the siren communication stream from the siren, threats will focus efforts, enabling countermeasures to be taken. For threats performing more active reconnaissance scanning efforts, decoys present attractive targets. Decoys can resemble systems and services threats will hope to potentially exploit or attack. When threats scan a network, decoys will be discovered because they are designed to respond to various service requests as if they were a fully functioning asset. The attacker will then focus efforts on the decoy, enabling countermeasures to be taken.
Adversaries utilize deception as part of their attack methodology. It makes perfect sense for OT professionals to also leverage easy to use and deploy deceptive elements to increase attack difficulty, discover attacker patterns, and prevent future attacks. False positives are always a concern with any security tool. However, with OT360 and OTRemote, false positive events and nuisance alerts are eliminated so that operators and security teams can act with confidence on genuine on-target alerts, and have the option to easily configure the solution in-line to active blocking of attacks with automated defensive actions.
- Figure 1 Illustrates how OT360 and OTRemote overcome common challenges with OT security.
- Figure 2 Depicts a notional architecture diagram that generally represents how the OT360 is deployed within OT and IT networks. Actual deployments will vary based on network architecture, scale, scope, etc.
- Figure 3 Depicts a notional architecture diagram that generally represents how the OTRemote is deployed within OT networks. Actual deployments will vary based on network architecture, scale, scope, etc.
Common OT Security Challenges addressed by PacketViper OT360 and OTRemote Solutions
Figure 1.
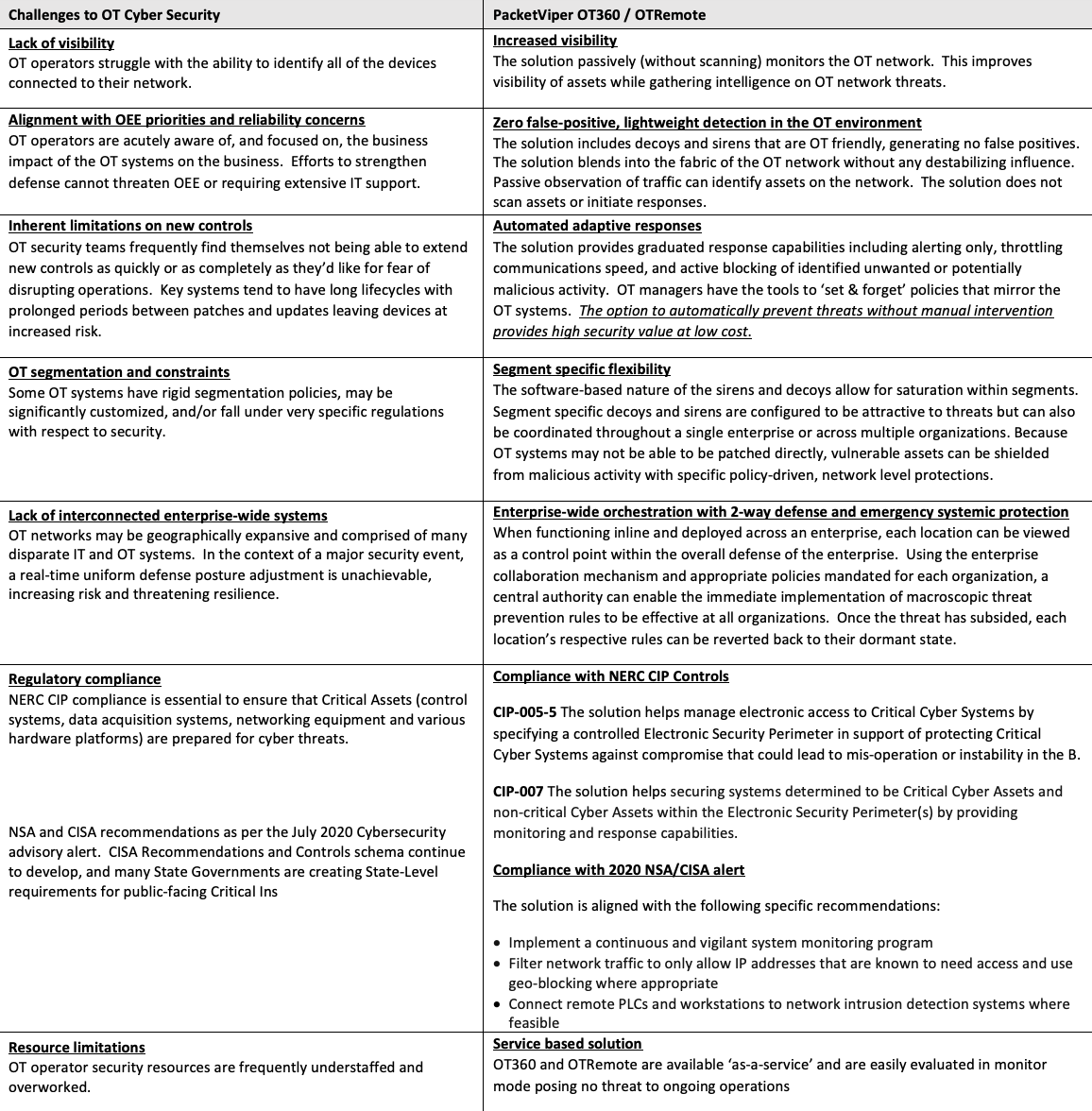
Figure 2. Notional diagram: Interconnected OT and corporate IT network defense architecture
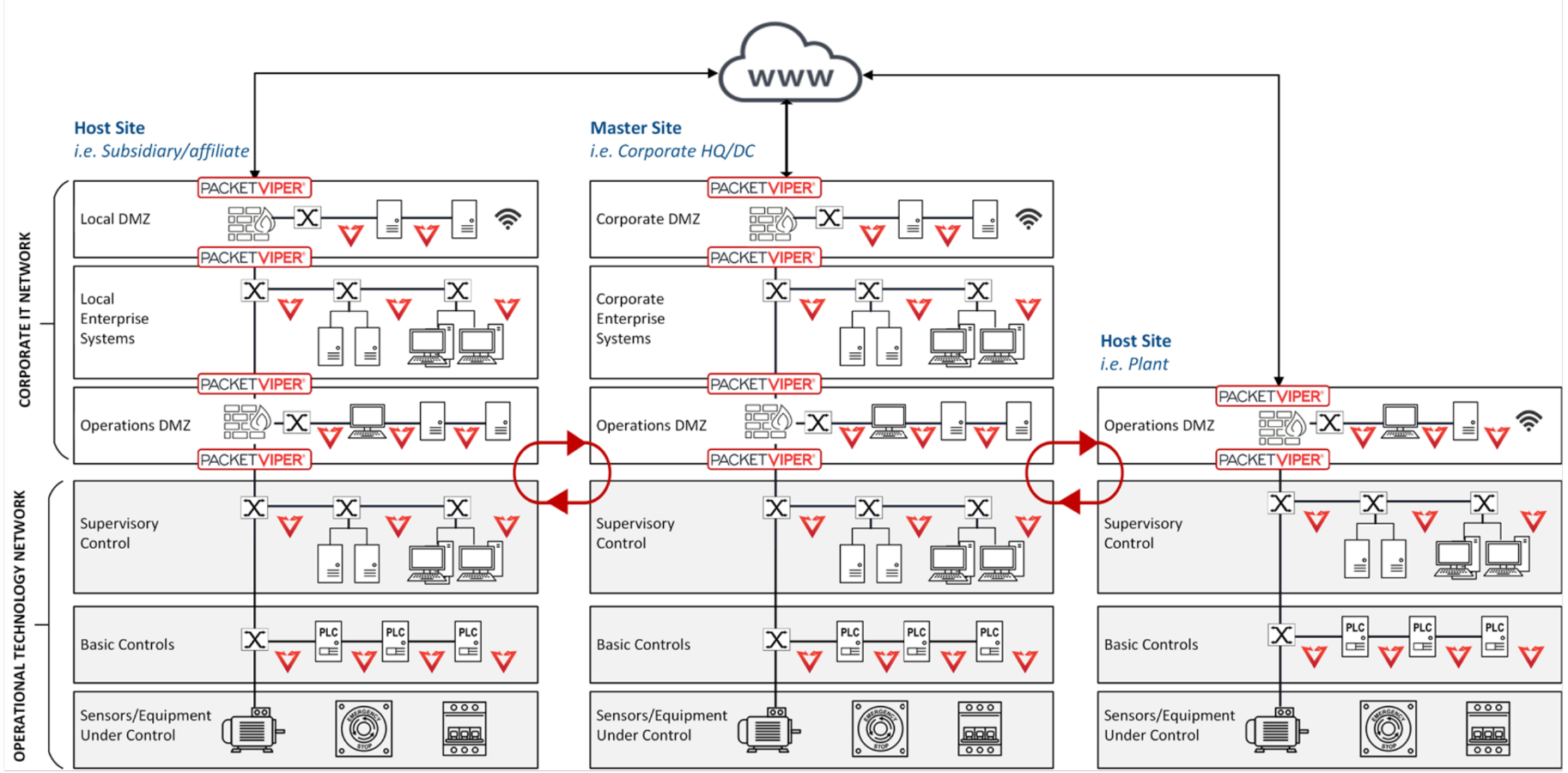
Figure 3. Notional PacketViper OTRemote Solution Architecture for Remote OT facilities
-(3).jpg)