IT360: Preemptive Network Defense
for the Zettabyte IP Traffic Era
Network Context is King
Despite advances by commercial “next-generation” firewall providers, cyber security breaches are an increasingly prevalent, dangerous, and costly problem for companies. As a result, liability and legal ramifications are an emerging business problem. The implementation of an off-firewall, precision multi-context and multi-layer approach for targeted defense has great potential to reduce the threat of cyber-attacks. Innovative advances in contextual filtering have enabled heretofore unseen levels of precision, agility, and user-friendliness, and this new and enhanced filtering should make the technology a viable and essential part of any comprehensive, layered approach to network security.Context is also critically important for traffic that is leaving any network, and as such, the multi-context filter should be applied in the stack directly behind the primary boundary security device. We call this approach a multi-context, multi-layer filtering capability of PacketViper IT360™.
The most common contextual element of contextual filtering is the Geographical element. However, there are other contexts to consider, each as important. PacketViper IT360 brings wire speed context filtering and the capability of automated threat defense to several elements in addition to geography, including Rate, Time, Port & Protocol, Company or Entity, Source/Destination Network, Source/Destination IP. A notional diagram of the multi-layer contextual filtering capabilities of the solution is represented in Figure 1.
Figure 1. Multiple Layered Network Connection Contexts
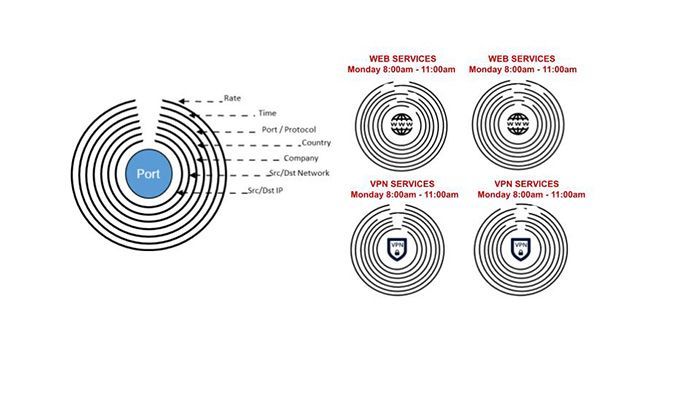
Boundary Protection In Both Directions
External and Internal Contextual Filtering.
Inside the boundary and internally oriented contextual filtering allow operators to immediately identify suspect behavior originating from internal assets and segments. Important security benefits are derived from this deployment and are immediately valuable to security operations team struggling under the load of too much network noise. Precision context brings unexpected and unsanctioned activity to the forefront, so that analysts can immediately respond, or choose to have the solution respond on their behalf.
Figure 2 - Security enhancements delivered by External AND Internal Multi-Context Multi-Layer Filtering
The First Layer: Geo-Targeted Cybersecurity and Network Defense
Cyber-attacks are a global phenomenon. Anyone with a computer or a smart phone and an Internet connection to launch an attack on a targeted victim anywhere in the world. Rented botnets can be used to distribute spam and phishing emails in addition to aiming an array of DDoS attacks at victim organizations. Geo-IP filtering is a network security tool that allows or denies network traffic, at the port level, based on geographical location, combined with a variety of other factors such as company, source/destination network, time and/or rate. Sometimes referred to as country filtering or blocking,
Geo-IP filtering allows the network to choose places in the world from which it will accept, and the places to which it will send network traffic.
Innovative designs in Geo-IP Filtering enable new and unparalleled levels of precision that allow businesses to prevent access to and from high-risk geographical areas without excluding potentially valuable customers or business, creating a multi-layer context filter.
Effective Geo-IP filtering is about much more than simply blocking a country. An effective Geo-IP filter must filter both inbound and outbound traffic as a first and last line of defense, with the country being only 1st element of the filtering process.
An Additional Layer for Defense-In-Depth
Geo-context filtering dramatically reduces that risk by improving the security of both the internal network and the DMZ, creating a synergistic and fundamental improvement in overall network safety.When placed at the start of the security filtering chain, enhanced Geo-IP filtering eliminates unnecessary traffic and threats, while simultaneously reducing the need for security inspections on the filtered unwanted and unneeded traffic —all of which ultimately result in improved performance throughout the most exposed area of the security chain, and throughout the security process.
With the Geo-IP filter positioned inline as an undetectable bridge, this layer quickly eliminates unwanted traffic for the remaining layers on the security chain while preventing outbound traffic to unwanted or suspect destinations.
PacketViper IT360 clients realize significant reduction in traffic on the external edge of their boundary protection device, with average results ranging from 50% to 70%, creating significant headroom on existing appliances.
Limitations of the Typical Network Security Approach
Despite the proven advantages of Geo-IP filtering there remains common misunderstandings of the fundamental concepts underlying its usage. Many popular firewalls claim to have Geo-IP filtering capabilities which generally offer either a geographical tool that is too rudimentary to be effective or too complex to be useful.The simpler tools resort to overly simplified methods that require entire nations to be excluded, costing a company potentially valuable markets or clientele.
Other firewalls offer overly complex geographical systems that are unwieldy and difficult to implement or rely on single contextual elements to simply operations. Companies who have attempted to use these features have experienced outages, delays, and slow speeds for browsing, email, web services, and remote access from 3rd Party vendors/suppliers/customers and internal users abroad were among the most common problems cited.
Most businesses find it necessary to make certain services such as Web, Mail, DNS, and FTP accessible to the public. This part of the network is also more accessible to hackers, and therefore is typically housed in a DMZ to protect the core of the network and its vital data. The DMZ is protected from the Internet to some extent by a firewall, and a second, more intensive firewall protects the internal network from any breaches of the DMZ. This is a straightforward design that usually provides good protection while providing essential services to your employees, customers, and vendors and has several underlying weaknesses that could cause significant to catastrophic damage to the enterprise.
With these types of serious limitations and problems with geographic screening tools, or with the occurrence of the first legitimate connection request from a particular country that was previously blocked by the firewall, many users simply disable the country blocking features in their firewalls and return to their initial approach. The current geographic filters fail because the firewalls lacked the ability to filter on a more precise basis than just the location of the computer or network. A multi-contextual analysis approach that considers additional variables – all at wire speed - will provide the level of detail required to more fully ascertain the security impact of any and every connection attempt.
Proxies and Geography
A critical component in the arsenal of cyber attackers – but one that can suggest a solution – is the crucial role of proxies and geography. Essential to the success of the attack is the use of Web proxies. By routing traffic through open proxies, the attackers attempt to bypass IP blocks.Attackers use tools that provide lists of open proxies and cycle through them after a fixed number of attempts. This allows cyber attackers to multiply their threats and to attack networks with virtual impunity. With multiple sources observing attack traffic originating from almost 200 unique countries/regions around the world, this global presence creates a myriad of opportunities for hackers and can overwhelm the ability of network firewalls and other security devices to keep up.
To maintain network security in an increasingly threatening future, it is absolutely essential to implement systems that shrink attackers’ options and prevent criminals from having unlimited attempts to penetrate vulnerable networks. Traditional network security systems are designed with an entirely defensive philosophy and are not capable of reducing hackers’ capacity to attack. Instead, security professionals should recognize that an enchained multi-context filtering capability is the best available solution for effectively reducing cyber-?attacker options. Multi-context filtering reduces attacker options by denying them use or direct network paths to or from networks, and enhanced filtering is particularly effective relative to typical security systems when hackers resort to the use of proxies.
IT360 does not drop connection requests like firewalls; the solution adds the offending IP to a blacklist that is then communicated via a central Enterprise Manager to every connected IT360 instance at wire speed. On the very next connection attempt, the offending IP will only encounter dead-air, and will never reach the compliance device of record – the firewall. This capability is an anchor tenant in the effort to eliminate unwanted, unneeded, and potentially malicious traffic. There are further enhancements available to expand this strategy, including variable external deception and moving target defense capabilities that are beyond the scope of this paper but are supported by other PacketViper products such as Deception360™ and OT360™
The Silent Killer of Network Security: Too Much Traffic (or Network Noise if you prefer)
While firewalls were evolving to provide much needed comprehensive filtering across the entire OSI stack, a new problem was brewing on the attacker front. Cyber-attacks have become a global phenomenon. Today anyone with a computer or a smart phone and an internet connection can launch an attack on a target victim anywhere in the world. Due to the ease with which attackers can cultivate a botnet and illicit services that rent the use of botnets, the cost to attack is cheap, getting cheaper, and more readily available. Rented and/or newly built botnets can be used to distribute spam and phishing emails, steal money, steal identities and propagate new malware. Cost is no longer a consideration as villains seek to aim high volume attacks at organizations.This is all exacerbated by the cultural need to be ‘constantly connected’. Organizations of all sizes desire to maintain real-time, constant connection to the internet results in a proliferation of devices which provide countless amounts of bot configuration options. The fluid nature of this expanding and contracting attacker landscape is impossible to address with firewalls and logging systems. Attackers leverage this advantage to distract network managers and constantly keep security teams on their heels in a reactive state. These attackers have countless resources and methods at their disposal and start with a simple reconnaissance scan, probe, or some other simple test of service limits. They hide these within everyday traffic patterns to distract administrators and gain intelligence to penetrate, incapacitate and/or extract data from a network.
A Root Cause Problem
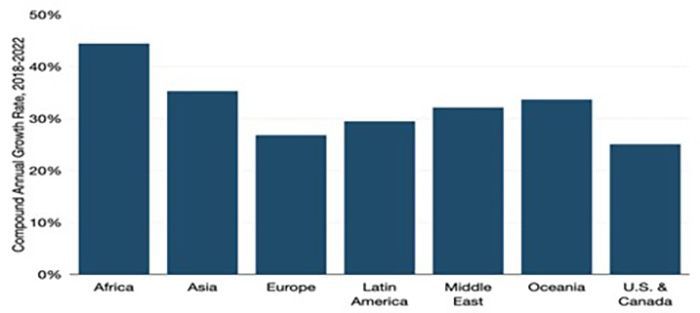
All of these increasing global IP traffic trends represent a root cause problem for network security managers, as evidenced in this chart from a recent Telegeography report on IP traffic trends, indicating that Global Internet Traffic has grown by 29% CAGR in 2022, setting a new record:Figure 2: Four Year Global IP Traffic Trends by Region
Unmanageable Log and Alert Volumes
Sprawling global IP traffic volumes are the prime contributor to the problematic amount of logging and alerting, which quickly becomes overwhelming for organizations of all size. Quite a number of Research Firms and Top Tier consultancies cite the volume of security alerts as the #1 or #2 operational challenge in security operations today. This is equally true of MSP, MSSP and SOC teams as it is for in-house network security teams. While larger enterprises are increasingly investing in security information and event manager (SIEM) applications, or Managed SIEM/SOC as a service, the real value of these solutions is compromised by the traffic volume problem. The increase in traffic correspondingly drives up the number of alerts, time required to check and time it takes to remediate. Many popular SIEM solutions and SIEM/SOC as a Service offering utilize volume-based pricing models. As a result, any illegitimate, unwanted, or un-needed traffic can dramatically increase tool expense, service fees, and overall security costs.
The Significance of an enhanced Multi-Context Based Approach To Network Security
Hacking, and cyber security are truly global problems. Spammers set up shop in co-locations, unregulated network space and vulnerable systems around the world. They are continually in motion and almost impossible to track, but multi-context filtering can help address this problem. Multi-context filters can reduce threats of any sort of cyber-attack, including botnets, zombie systems, malware infected web servers, and email viruses, as well as the costs and liabilities that go along with them. Outbound context filtering helps combat these types of breakouts by limiting their ability to operate freely around the world. In other words, context filtering not only stops threats from penetrating the network, but it also addresses the possibility that any asset on the network - employee’s laptops, cell phones, shared workstations, or other local device could carry a threat and transmit it to the Internet via the network.
For threats that have already penetrated the network, outbound context filtering minimizes the change that the threat will be able to successfully communicate with remote command and control assets.
It is important to remember that in a typical security system, a port opened through the firewall allows equal access to anyone in the world. Operators must create a myriad of custom firewall rules to address this reality. If the organization requires dozens or hundreds of open ports, the rule problem can grow substantially, and create problems down the road in an emergency situation. One misplaced ANY-ANY / ANY-ALL override rule to overcome an obscure firewall blocking in a rule jungle can spell disaster. Given the statistics on the continuous probing of the network edge, and the volume of attacks that a network is likely to face, consider these questions:
- How much business do we conduct in a certain nation?
- How many clients do we have in another?
- How likely is it that we should want to market our business across the world?
- What ports and protocols are required for any communication?
- What volume of traffic is expected as normal?
- At what time of the day or day of the week?
Balancing the results of responses to these questions with the volume of cyber-attacks originating in any of those countries and provide access to the network according to the dictates of business needs, not on an arbitrary all-?or-?nothing basis.
This sort of controlled and measured access to the network is exactly what multi-context filter enables.
Enhanced Multi-Context Filtering - Granularity and Precision
Organizations need an easy-to-use context filtering system with great flexibility, customization capability, and precision. Extensive research proves that the key to solving the granularity and precision problem would involve the ability to simultaneously filter by country, at the network port level, and at the entity level, with expected rate, date, time, direction, and specific IP address filters enabled. This method- PRECISION – To target extremely specific filtering elements avoiding blacking out other stacking connection requirements
- CUSTOMIZATION – To quickly and accurately specify which countries and companies are permitted to access specific network ports, etc., instead of completely blocking them, eliminating unwanted network traffic and focusing on traffic that is important to the environment. Users need to have the ability to intelligently override geo filtering using constantly updated intelligence lists of global businesses and high-risk networks.
- FLEXIBILITY – To modify to meet constantly changing needs and markets.
IT360 dashboards have clickable events accompanied by an individualized NetCheck™ capability that allows operators to quickly view - in real time - the traffic entering or leaving an environment, the IPs that are sending and receiving traffic, and much more. Operators can click on any log entry and quickly see additional details such as associated networks, source country, region, city, ISP, and RDNS. The solution also provides the capability to act on the traffic anonymously or from the dashboard.
- PRECISE – Filtering at the network level with stacking context attributes both bound and outbound
- CUSTOMIZABLE – Easily applied updated intelligence lists of global business IP address space and high-risk networks
- FLEXIBLE – A quick and simple point and click method with all the necessary information on the dashboard.
- BUDGET FRIENDLY – IT360 dramatically reduces cost and burden on important network security components, solutions, and human resources. For many organizations the solution returns more to the budget than the cost to own and operate.